Teslamate Exposed: When Your Tesla Data Is Out in the Open
The Silent Problem of Teslamate
Hello everyone! Today we’re going to talk about a serious privacy problem affecting thousands of Tesla owners: exposed Teslamate installations. If you’re a Tesla owner or simply interested in IoT security, this post will be very revealing to you.
During my investigation in the OSINT field, I stumbled upon something I didn’t expect: hundreds of Teslamate dashboards completely exposed on the internet, showing intimate data about their owners’ lives without them being aware of it.
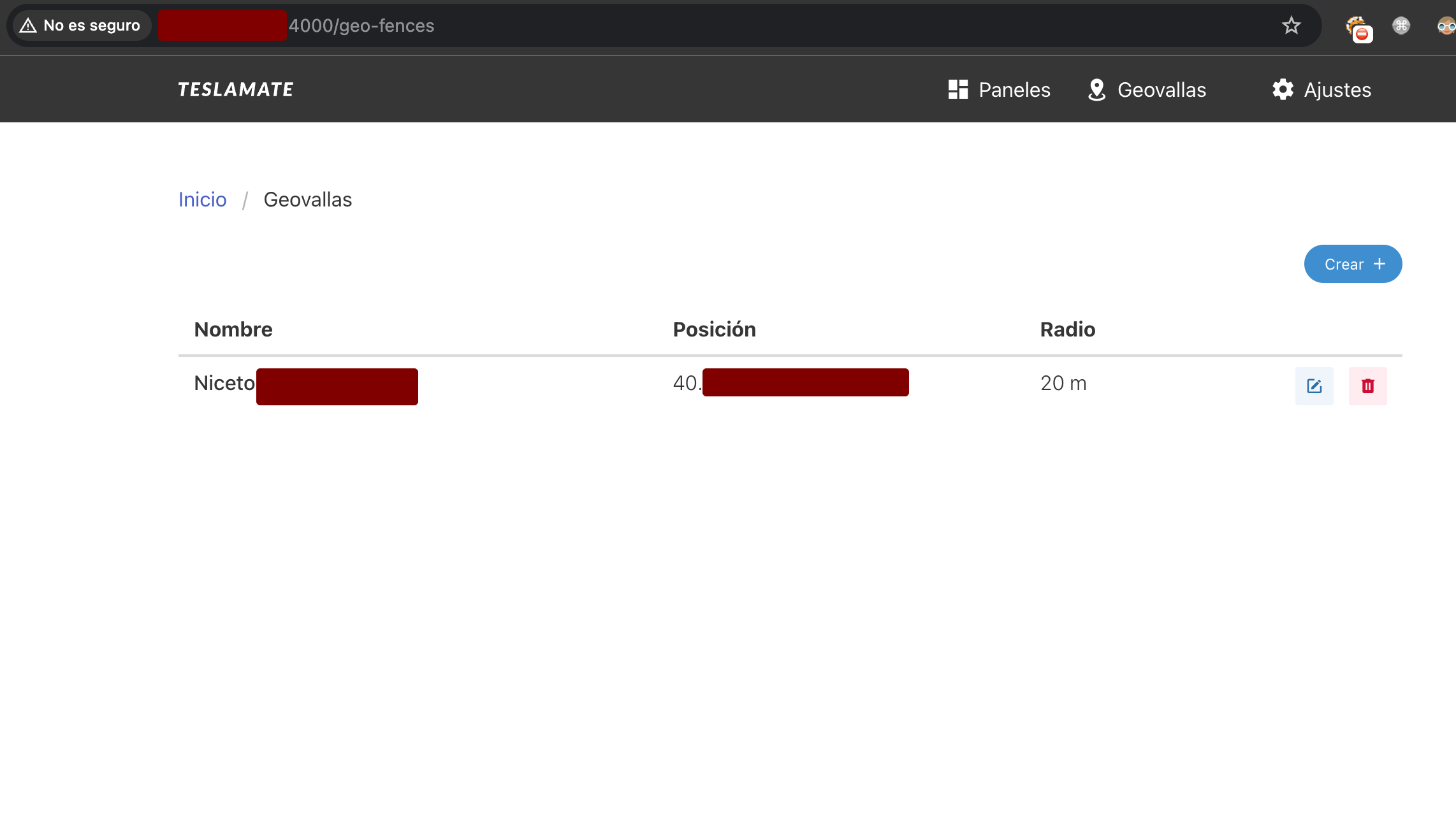
What is Teslamate?
Teslamate is a very popular open-source tool among Tesla owners that allows monitoring and recording all vehicle data in detail. Its popularity is due to Tesla not providing these functionalities natively, leaving users with little historical data about their vehicle usage.
The tool connects to the official Tesla API and continuously collects vehicle information, storing it in a PostgreSQL database. It then uses Grafana to create interactive dashboards that show:
- Trip logs with exact locations and complete routes
- Detailed charging data with energy efficiency per session
- Vehicle usage patterns and consumption analysis
- Driving statistics with speed, acceleration, and braking metrics
- Custom geofences to monitor specific locations
- Software update history of the vehicle
- Battery degradation and vehicle health analysis
The Configuration Problem
The problem arises because many users are exposing these installations directly to the internet without any type of authentication. Teslamate’s default configuration doesn’t include robust security measures, and many users, following basic tutorials, end up exposing their data without realizing it.
Exposed Data
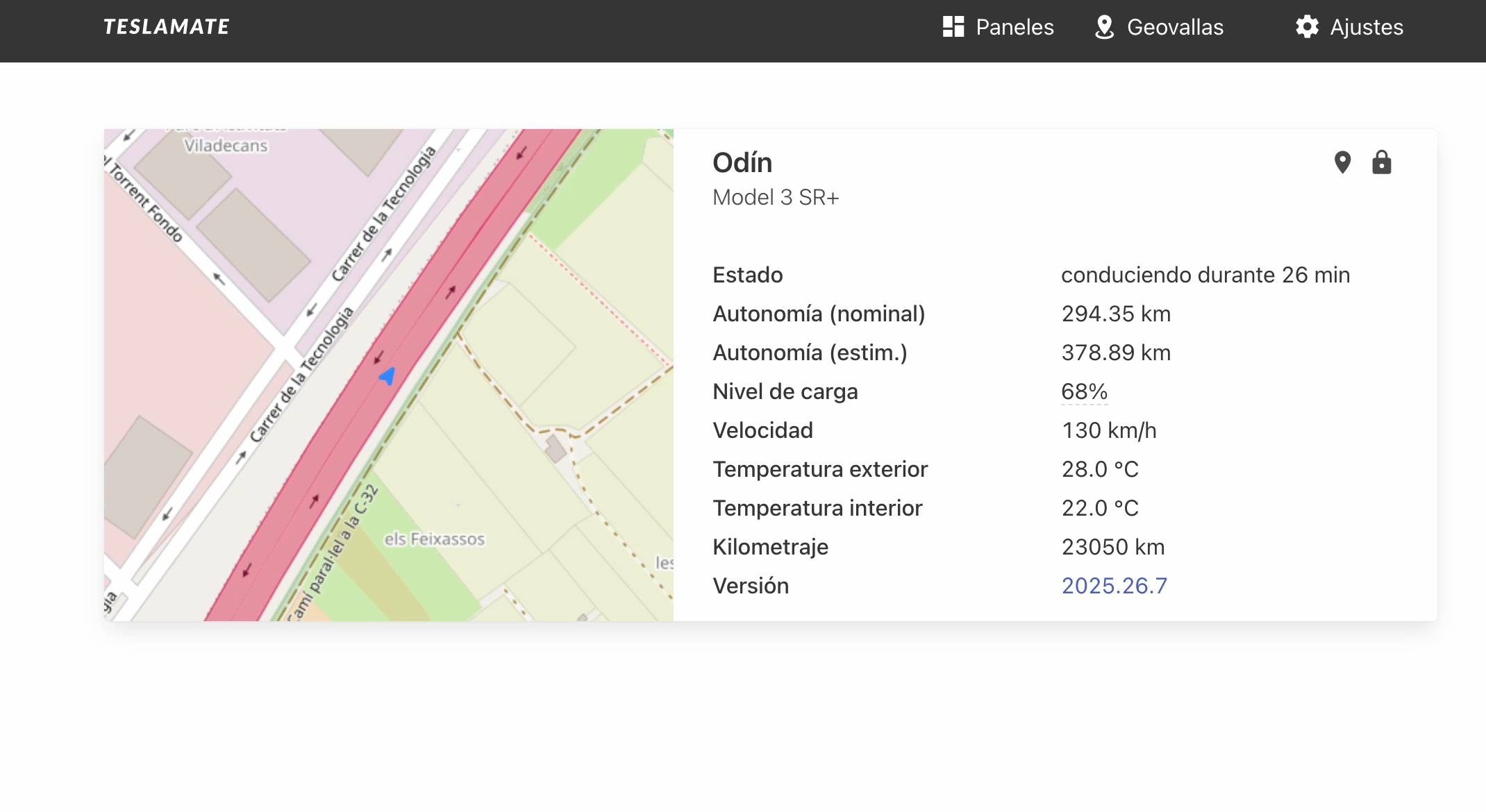
During my investigation, I found hundreds of Teslamate installations completely accessible from the internet. The information that can be obtained includes:
📍 Location Data
- Owner’s exact home address
- Regular workplace
- Frequent destinations
- Real-time vehicle location
🚗 Vehicle Information
- Specific Tesla model
- Total mileage
- Battery charge status
⏰ Life Patterns
- Departure and arrival times at home
- Daily and weekly routines
- Periods of absence from home
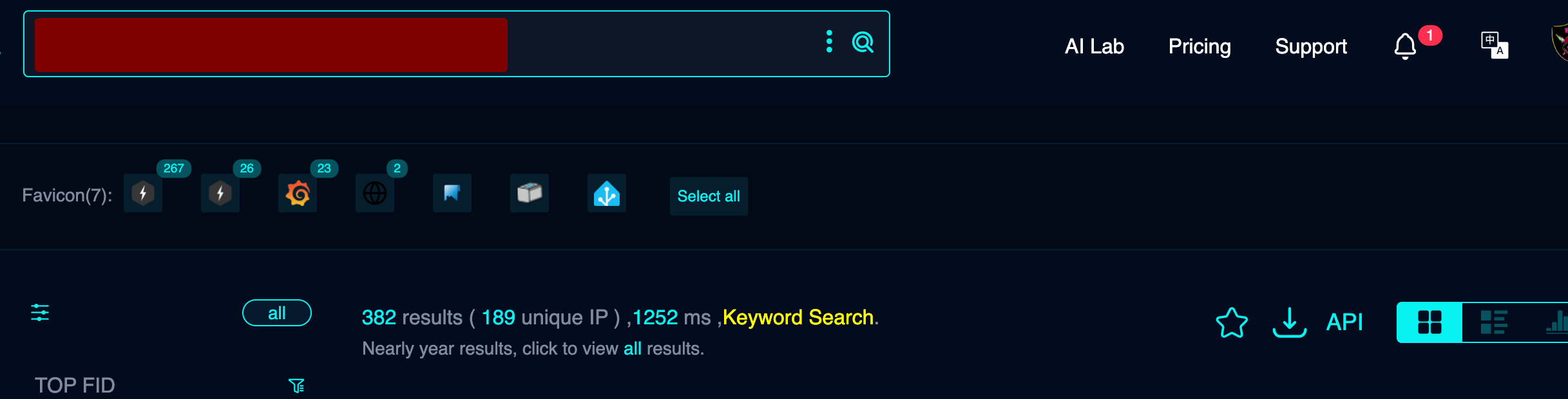
Search Methodology
To find these installations I used various OSINT (Open Source Intelligence) techniques combining tools like Shodan, Censys, and Google Dorking to locate exposed services.
The results have been alarming:
- +500 exposed installations found
- Affected countries: United States, Germany, Netherlands, United Kingdom, Australia
- Types of exposure: Completely open dashboards and accessible APIs
Video Demonstration
In the following video I show the complete search and analysis process:
If you can’t see the video:
Risks for Owners
The exposure of this data carries serious risks that go far beyond what many owners might imagine:
🏠 Physical Security
- Exact home identification with meter precision
- Predictable absence patterns that allow planning robberies
- Exposed family routines including work and school schedules
- Vacation periods clearly identifiable when the house is empty
- Frequent locations like gyms, shopping centers, children’s schools
🕵️ Stalking and Harassment
- Movement tracking in real-time for stalkers
- Future location prediction based on historical patterns
- Personal behavior analysis and intimate routines
- Relationship identification through shared locations
💰 Financial and Legal Risks
- Targeted vehicle theft when it’s known to be away from the garage
- Insurance problems for not adequately protecting information
- Employment discrimination based on mobility patterns
- Blackmail using information about compromising locations
📊 Family Privacy Violation
- Minor exposure through routes to schools and activities
- Health habits revealed by visits to hospitals or clinics
- Economic situation inferred from visited locations
- Personal relationships exposed through location patterns
Security Recommendations
For Teslamate Users
Take these measures immediately:
🔐 Mandatory Authentication
- Configure strong passwords in Grafana (minimum 12 characters)
- Disable anonymous access completely
- Implement two-factor authentication (2FA) when possible
- Change default credentials if you’ve ever used them
- Review configured users and remove unnecessary accounts
🌐 Access Restriction
- NEVER expose Teslamate directly to the internet
- Use personal VPN (Wireguard, OpenVPN) for remote access
- Configure IP whitelisting if you need access from specific locations
- Use SSH tunnels as a secure alternative
- Consider services like Tailscale for easy private networks
🛡️ Reverse Proxy and Encryption
- Implement nginx or Apache with additional HTTP basic authentication
- Use valid SSL certificates (Let’s Encrypt is free)
- Configure rate limiting to prevent brute force attacks
- Implement fail2ban to automatically block malicious IPs
- Configure security headers (HSTS, CSP, X-Frame-Options)
🔍 Monitoring and Maintenance
- Review access logs regularly
- Configure alerts for unusual access
- Keep Teslamate updated with the latest security versions
- Perform encrypted backups of your data
- Audit your configuration monthly
Conclusions
This investigation demonstrates that the problem of personal data exposure in IoT tools is much more common than we think. Teslamate is just the tip of the iceberg.
Lessons Learned
- Never expose internal services directly to the internet
- Security through obscurity doesn’t work
- Regularly review your online exposures
- Secure by default should be the guiding principle
This type of exposure will continue to grow with the proliferation of IoT devices. It’s crucial that both developers and users take proactive measures to protect privacy.
Did you find this post interesting? Share it and help create awareness about the importance of security in our connected devices!