Vulnerabilities in Government Services: XSS and IDOR in Digital Platforms
Introduction: Vulnerabilities in Critical Services
Hello everyone! Today we’re going to analyze a concerning discovery: multiple security vulnerabilities in a government digital platform for fiscal services. During a security audit, I identified three critical vulnerabilities that affect the security and privacy of citizens.

Discovery Context
The vulnerabilities were found in the virtual assistant and document management systems of a government entity, services used daily by citizens for administrative consultations and official documentation management.
Identified Vulnerabilities
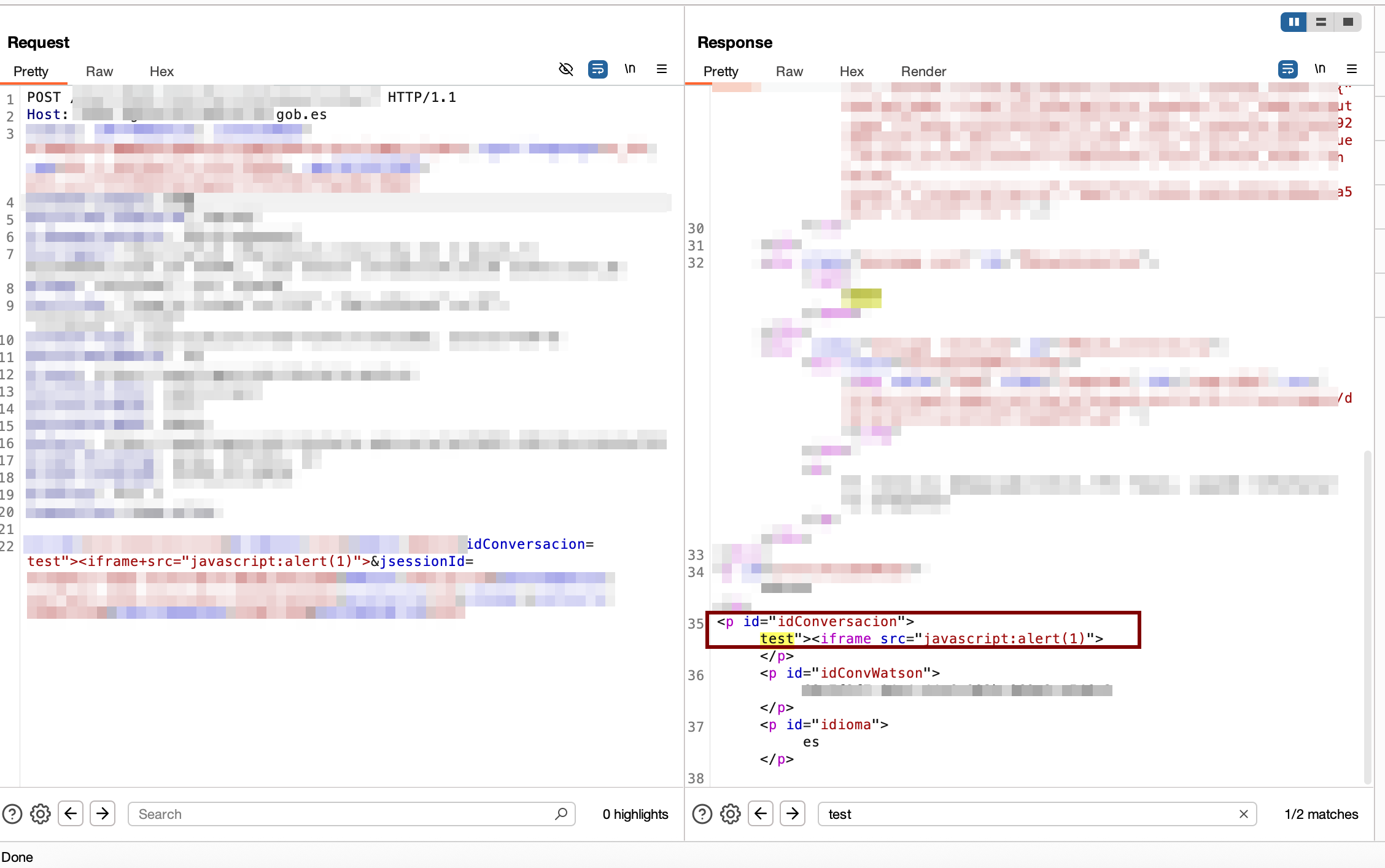
🚨 Vulnerability 1: Reflected XSS in AsistenteController
Description
Reflected Cross-Site Scripting (XSS) in the conversation parameter of the virtual assistant endpoint.
Technical Details
- Affected endpoint:
/path/to/assistant/controller - Vulnerable parameter:
conversationId - Type: Reflected XSS
- Method: POST
Proof of Concept Payload
conversationId=test"><iframe src="javascript:alert(1)">
Impact
- JavaScript execution in the context of the official domain
- Potential cookie theft and session tokens
- Unauthorized access to sensitive user data
- Page content modification
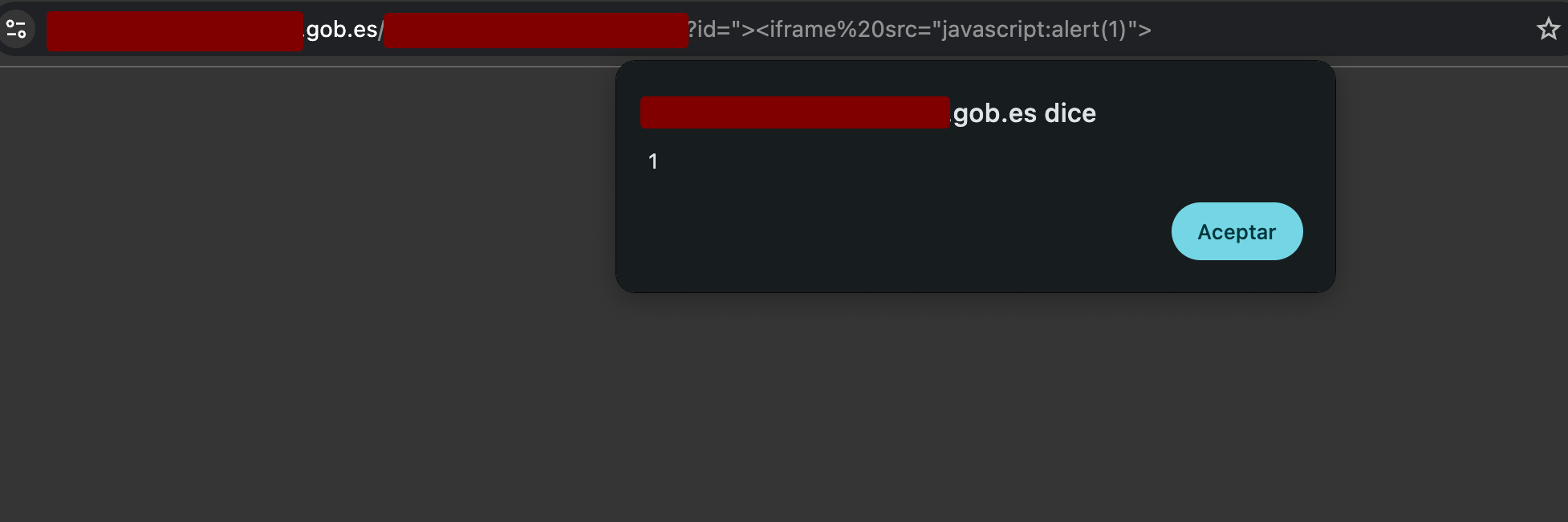
🚨 Vulnerability 2: Reflected XSS in DetallePDF
Description
Reflected Cross-Site Scripting (XSS) in the id parameter of the document management endpoint.
Technical Details
- Affected endpoint:
/path/to/document/handler - Vulnerable parameter:
documentId - Type: Reflected XSS
- Method: GET
Exploitation URL
https://example-gov-site.com/path/to/document/handler?documentId=<iframe src="javascript:alert(1)"
Impact
Similar to the previous one, but with the additional advantage of being exploitable via GET, facilitating phishing and social engineering attacks.
🚨 Vulnerability 3: IDOR - Unauthorized Access to Conversations
Description
Insecure Direct Object Reference (IDOR) that allows access to private conversations of other users through ID parameter manipulation.
Technical Details
- Affected endpoint:
/path/to/document/handler - Vulnerable parameter:
documentId(sequential IDs) - Type: IDOR (Unauthorized Access)
Exploitation Example
https://example-gov-site.com/path/to/document/handler?documentId=[INCREMENTAL_ID]
Exposed Data
- Full name and identification number of citizens
- Complete conversations with the virtual assistant
- Specific administrative consultations
- Date and time of interactions
- Sensitive data related to official procedures
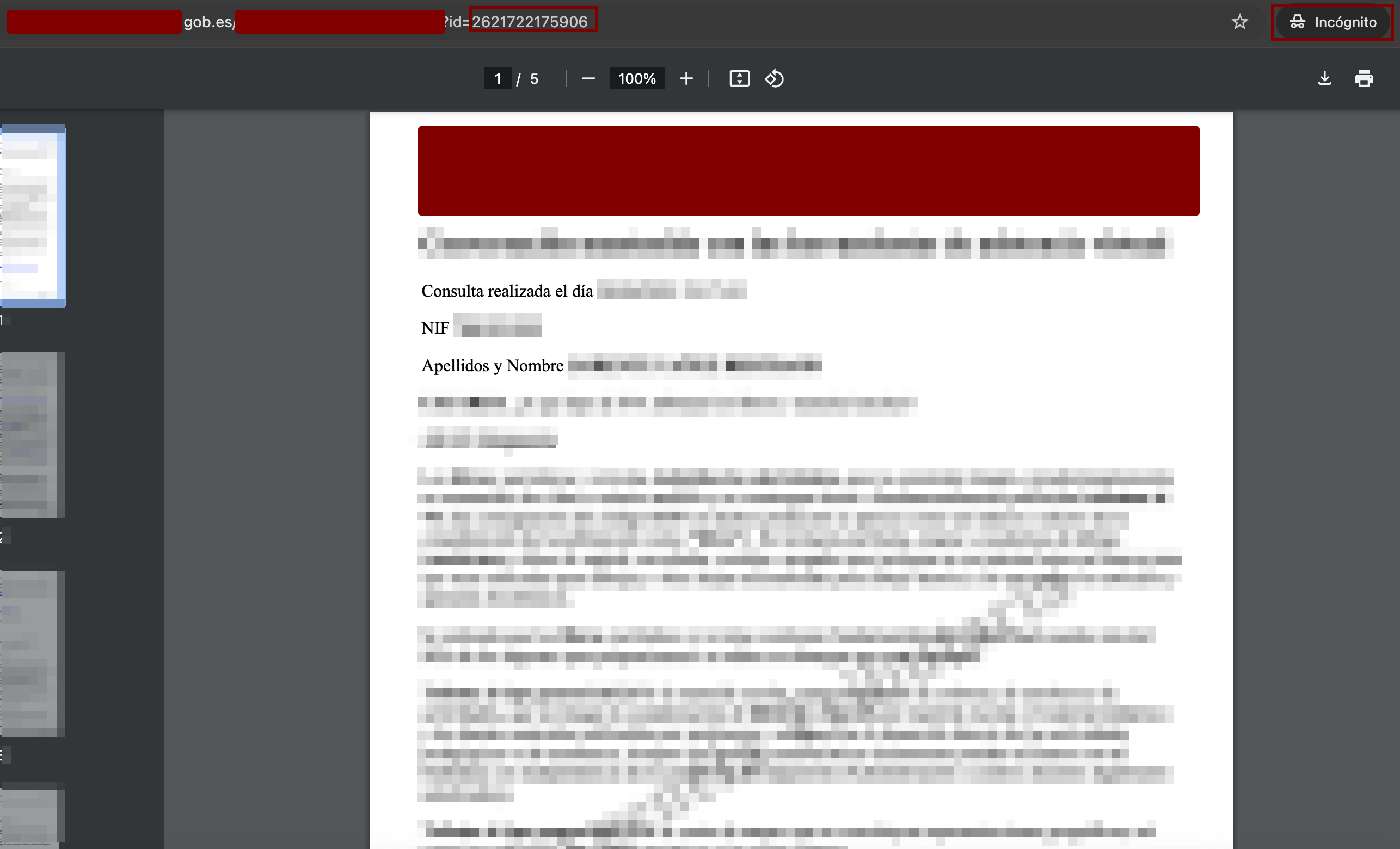
Example of Exposed Data
Compromised Personal Information
In controlled tests, access was gained to information such as:
ID: [ANONYMIZED_NUMBER]
Last Name and Name: [CENSORED_PERSONAL_DATA]
Query made on: [ANONYMIZED_DATE]
USER: How do taxes apply to educational products?
USER: Payment methods available for official forms
USER: Query about fiscal regulations for renovations
Risks and Impact
🎯 For Citizens
Privacy Violation
- Exposure of personal fiscal data
- Unauthorized access to tax consultations
- Revelation of sensitive economic information
Security Risks
- Identity theft through Tax ID and personal data
- Social engineering using real tax information
- Targeted tax fraud based on obtained data
🏛️ For the Administration
- Loss of citizen trust
- Data protection regulation non-compliance
- Potential sanctions from regulatory bodies
- Compromise of internal systems
Mitigation Recommendations
🛡️ Key Recommendations
For the Organization
- Strict validation of input parameters
- Escaping of special characters
- Implementation of robust CSP
- Authorization verification on endpoints
- Anti-CSRF tokens
// Mitigation example
$id = htmlspecialchars($_POST['id'], ENT_QUOTES, 'UTF-8');
if (!isAuthorized($userId, $docId)) return error403();
For Citizens
- Review URLs before clicking
- Log out after use
- Monitor personal access
Conclusions
This case demonstrates the importance of:
- Regular audits in public services
- Security training for developers
- Robust review processes
Security in digital public services is non-negotiable. It’s the administrations’ responsibility to guarantee the highest security standards.
This analysis is published for educational purposes and to raise awareness about the importance of security in digital public services.