XSS Filter Bypass in Educational Web Application: SVG-Based Techniques
Introduction: XSS Filter Analysis
During a security assessment, a Cross-Site Scripting (XSS) vulnerability was identified in an educational web application from the Junta de Andalucía that implemented a security filter to prevent such attacks. However, this filter had limitations that allowed bypass through specific techniques.
The XSS Filter Detection
The application implemented a filtering system that detected common XSS patterns. When attempting to inject malicious code, the system responded with a detailed error:
HTTP Status 500 – Internal Server Error
Type Exception Report
message An exception occurred processing JSP page
java.lang.SecurityException: Possible XSS attack attempt: "><img src=test >
Filter System Analysis
The stack trace revealed valuable information about the implementation:
sadiel.cec.xss.XSSManager.comprobarAtaqueXSS(XSSManager.java:56)
sadiel.cec.xss.ParametrosPeticionXSS.comprobarAtaque(ParametrosPeticionXSS.java:84)
sadiel.cec.xss.XSSFilter.doFilter(XSSFilter.java:52)
This information indicates that:
- The filter is implemented as a Java servlet
Filter - It uses an
XSSManagercomponent for detection - It processes all HTTP request parameters
Bypass Technique: SVG Elements
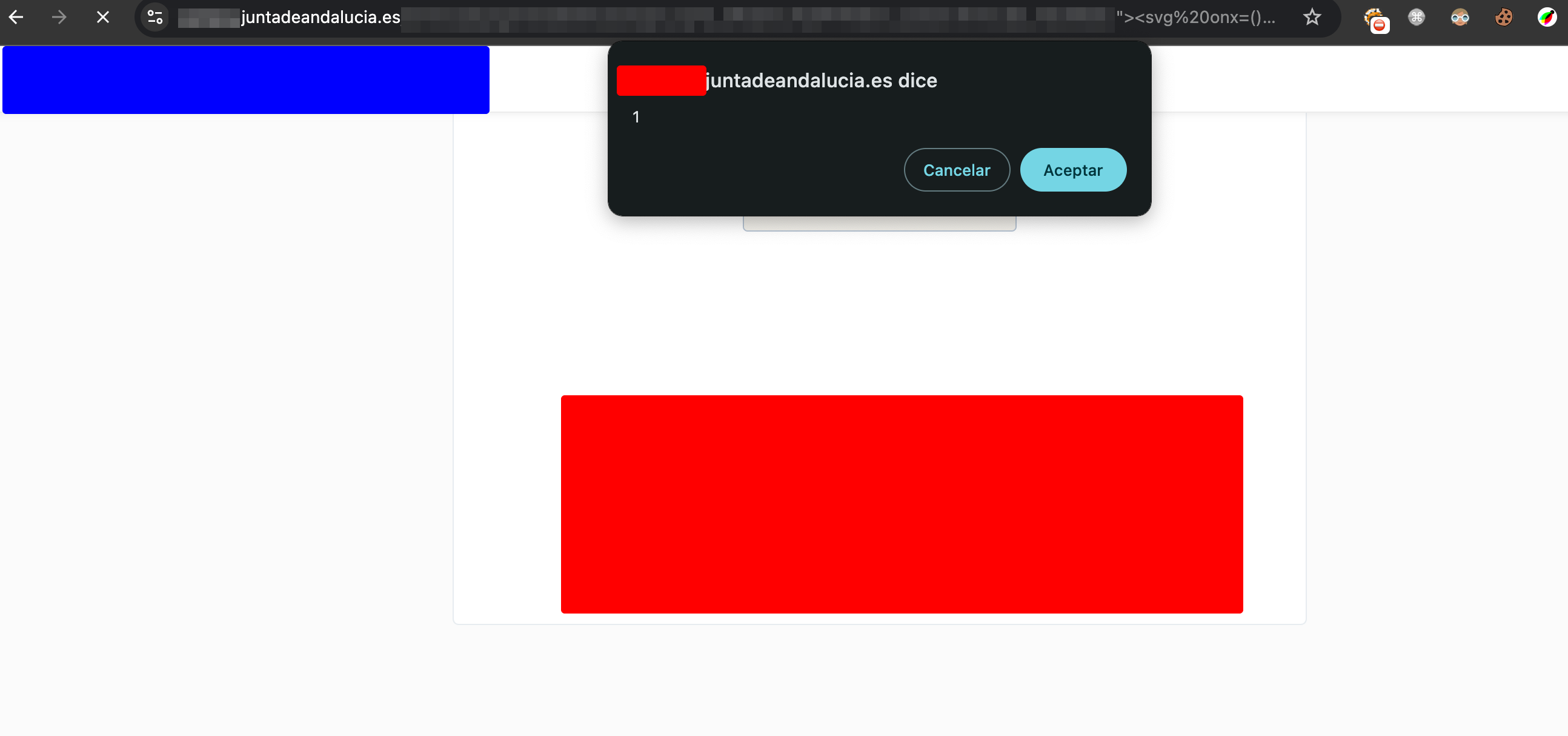
The Successful Payload
The bypass was achieved using SVG (Scalable Vector Graphics) elements with unconventional event handlers:
<svg onx=() onload=(confirm)(1)>
Why Does This Bypass Work?
- SVG Element: SVG elements are valid HTML5 and less common in blacklists
- Non-Standard Event Handler:
onx=()is an attribute that doesn’t trigger events but confuses the parser - Main Handler:
onload=(confirm)(1)uses valid but uncommon JavaScript syntax - Parentheses vs Quotes: Using parentheses instead of quotes can evade certain filters
Technical Payload Analysis
// Payload breakdown:
<svg // Valid HTML5 element
onx=() // Fictitious attribute that may confuse parsers
onload= // Real event handler that executes on load
(confirm)(1) // Valid JavaScript: executes confirm(1)
> // Element closure
Limitations of Blacklist-Based Filters
This case demonstrates common limitations of XSS filtering systems:
1. Dependence on Known Patterns
- The filter detected
<img src=but not<svg onload= - It focused on common HTML elements
2. Incomplete Parsing
- Did not properly analyze alternative JavaScript syntax
(confirm)(1)vsconfirm(1)- both valid syntax
3. Lack of Context
- Did not consider modern HTML5 context
- SVG introduced new attack vectors
Security Recommendations
For Developers:
- Whitelist over Blacklist: Allow only specifically authorized content
- Context-Aware Encoding: Encode according to context (HTML, JavaScript, CSS, etc.)
- Content Security Policy (CSP): Implement CSP to mitigate XSS
- Server-Side Validation: Never rely solely on client-side validation
For System Administrators:
- Updated WAF: Keep Web Application Firewall rules updated
- Detailed Logging: Log all bypass attempts for analysis
- Regular Testing: Perform periodic penetration testing
Impact and Responsibility
⚠️ Important Note: This analysis is presented for educational and research purposes only. The report was conducted following responsible disclosure principles and vulnerabilities were reported through official channels.
Conclusions
This case illustrates the importance of:
- Implementing robust filters that consider modern attack vectors
- Not relying solely on blacklists for content filtering
- Keeping defenses updated against new bypass techniques
- Performing regular audits of security systems
XSS filters based on simple patterns are insufficient against attackers who understand the limitations of these systems. It is essential to adopt a defense-in-depth approach that combines multiple mitigation techniques.
This analysis is published solely for educational and web security research purposes. All testing activities were conducted under ethical principles and responsible disclosure.